Overview
These APIs are designed to enable a variety of use cases where in-person payments are necessary. Here are a few examples of how this API can be used:- Self Server Kiosk
- Point of Sale
- Vending Machines
Terminal Devices Supported
How It Works
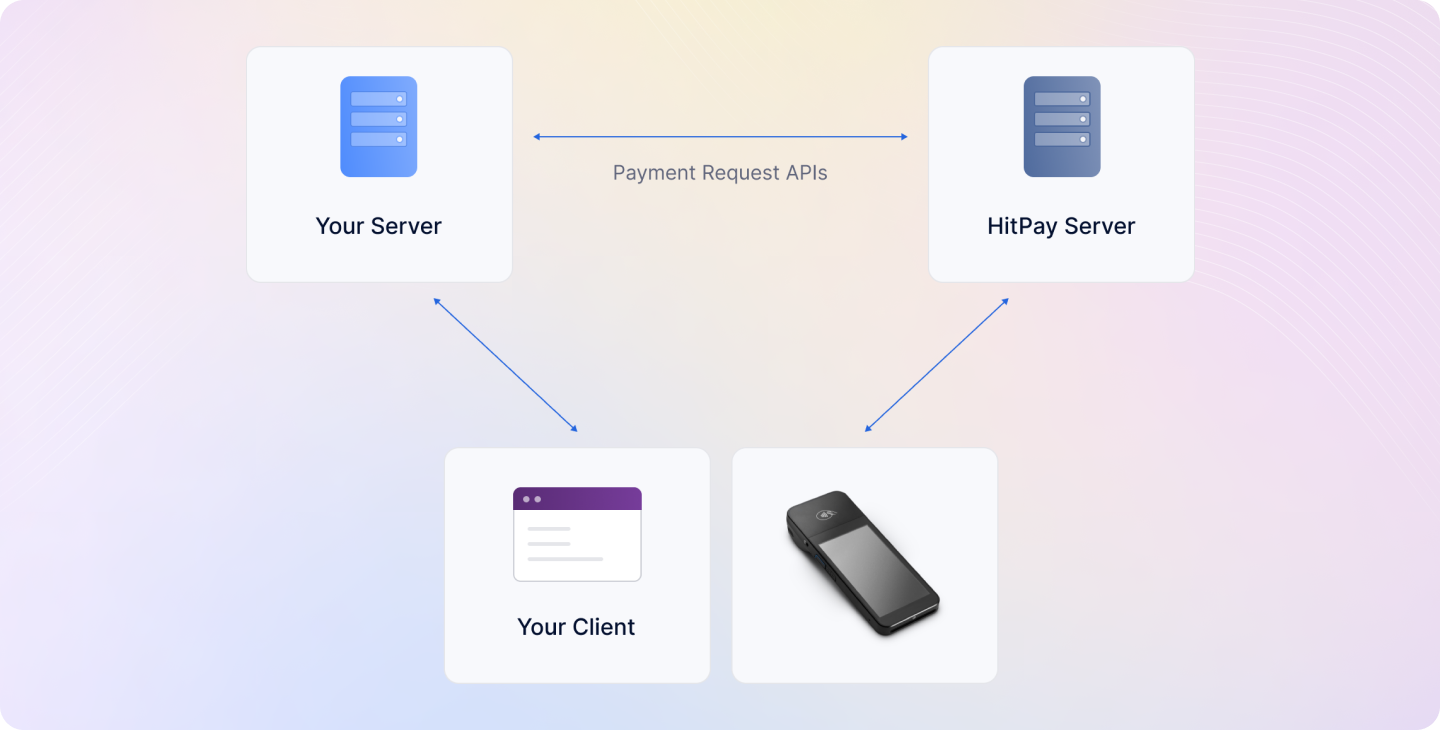
- Your client device (e.g., POS, Kiosk) sends a request to your backend server to initiate the payment process.
- Your backend server calls the Payment Request API with the payment method set as “wifi_card_reader”.
- HitPay initiates the payment process on the card reader that is already connected to the wifi.
- Your customer presents their card to the card reader and completes the payment process.
- HitPay sends a webhook to your backend server with the payment status information.
- Your backend server receives the webhook and updates the order status accordingly.
Setup Your Reader
Before you can use the In-Person Payments using Payment Requests API, you’ll need to order a card reader and complete the setup process. Here’s what you need to do:Displaying Payments on the Terminal
After switching your terminal to Standalone mode:- On the login screen, tap the button on the top left corner.
- Select In-Person Payment API from the menu.
- The terminal will now display the In-Person Payment API screen, allowing you to accept card and QR payments.
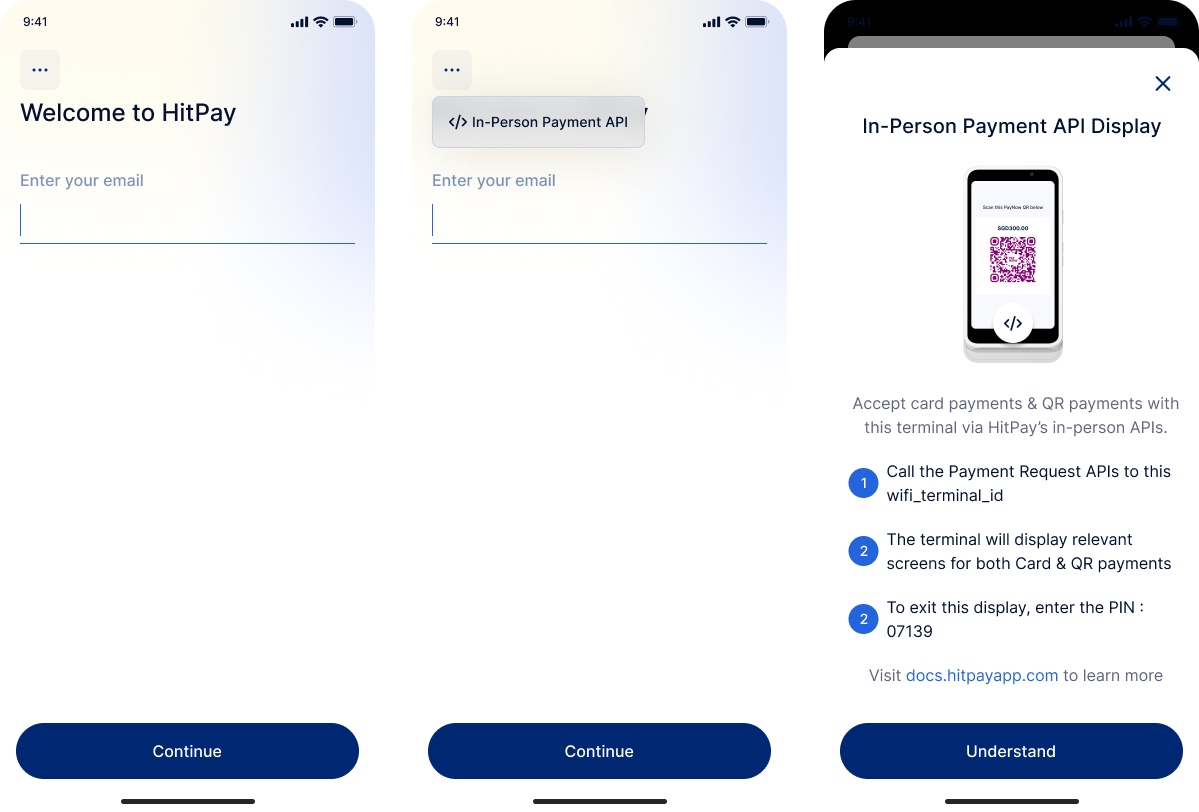
- The display will show the HitPay logo.
- If a QR payment method is selected, the relevant QR code will be displayed for the customer to scan.
- If a card payment method is selected, the display will show instructions to tap, insert, or swipe the card.
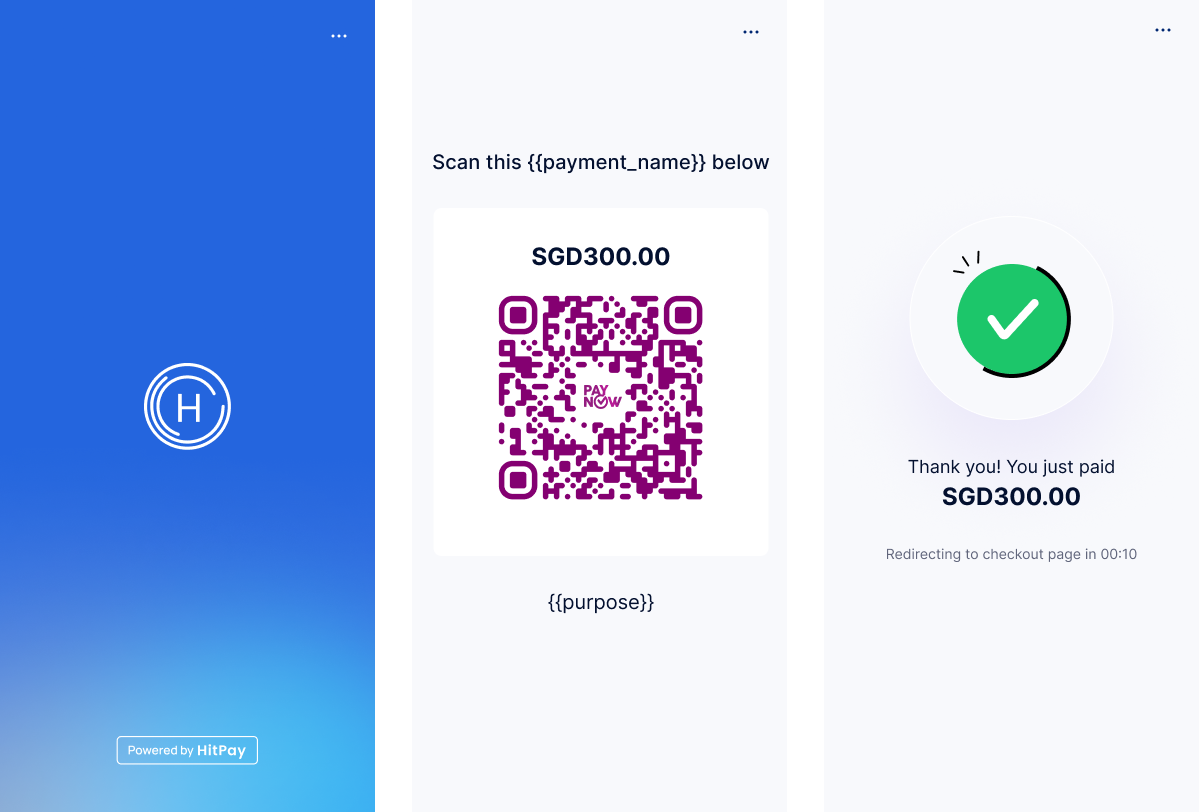
To quit the In-Person Payment API mode, please enter the PIN:
07139.Ingenico DX4000
For HitPay All-in-One Ingenico DX4000 Terminal in Philippines, you have two options:- To accept QR payments only, follow instructions above. No log in is needed.
- To accept both QR and cards payments, log in to your HitPay account, go to Settings > In-person Payment > key in PIN:
8888(use the same PIN to exit mode)
Payment Methods
The in-person payment API supports two main payment methods:1. Card Payments
Accept physical card payments (credit/debit cards) using the card reader.2. QR Payments
Accept QR code payments where customers scan the QR code displayed on the card reader screen.Create Payment Requests via APIs
Once you have all the details from the client and are ready to collect payments, use this API to create a payment request. EndpointInitiating Card Payments
To initiate a card payment, follow these steps:- Create Payment Request: Use the Payment Request API with
payment_methods[]set towifi_card_reader - Card Reader Activation: The card reader will automatically activate and display “Ready for Payment”
- Customer Interaction: Ask your customer to insert, tap, or swipe their card on the reader
- Payment Processing: The card reader will process the payment and display the result
- Webhook Notification: You’ll receive a webhook with the payment status
Query Parameters
Mandatory fields are amount and currency| Parameter | Description | Example |
|---|---|---|
| amount | The amount related to the payment | 2500.00 |
| payment_methods[] | Indicate that the request is for in-person payments using a wifi card reader | wifi_card_reader |
| currency | In-Person payments only support the home currency of your business | SGD |
| wifi_terminal_id | The reader ID can be found in your dashboard under “POS > Terminals”. For Ingenico DX4000 PH terminals, use the last 8 digits of your terminal SN located at the back of your terminal. | tmr_123123123 (WisePOSE), MD9Q2493 (Ingenico PH), S1F2-001582391283 (All-in-One S1F2) |
Initiating QR Payments
To initiate a QR payment, follow these steps:- Create Payment Request: Use the Payment Request API with
payment_methods[]set to any supported QR payment method andgenerate_qrset totrue - QR Code Display: The card reader will automatically display a QR code on its screen
- Customer Scanning: Ask your customer to scan the QR code using their mobile payment app (e.g., PayNow, GrabPay, etc.)
- Payment Processing: The customer completes the payment through their mobile app
- Webhook Notification: You’ll receive a webhook with the payment status
Supported QR Payment Methods
For QR payments, you need to use one of the supported QR payment methods. See the complete list of supported QR payment methods.Query Parameters
| Parameter | Description | Example |
|---|---|---|
| amount | The amount related to the payment | 2500.00 |
| payment_methods[] | One of the supported QR payment methods (e.g., paynow_online) | paynow_online |
| currency | In-Person payments only support the home currency of your business | SGD |
| wifi_terminal_id | The reader ID can be found in your dashboard under “POS > Terminals”. For Ingenico DX4000 PH terminals, use the last 8 digits of your terminal SN located at the back of your terminal. | tmr_123123123 (WisePOSE), MD9Q2493 (Ingenico PH), S1F2-001582391283 (All-in-One S1F2) |
| generate_qr | Set to true to generate QR code data | true |
Response
The response will include aqr_code_data object, which contains the data to be converted into a scannable QR code (qr_code).
Example Response for QR Payment Request
Example Response for QR Payment Request
The card reader will automatically determine whether to show a QR code or activate card reading based on the available payment methods and customer preference.
Handle Webhooks
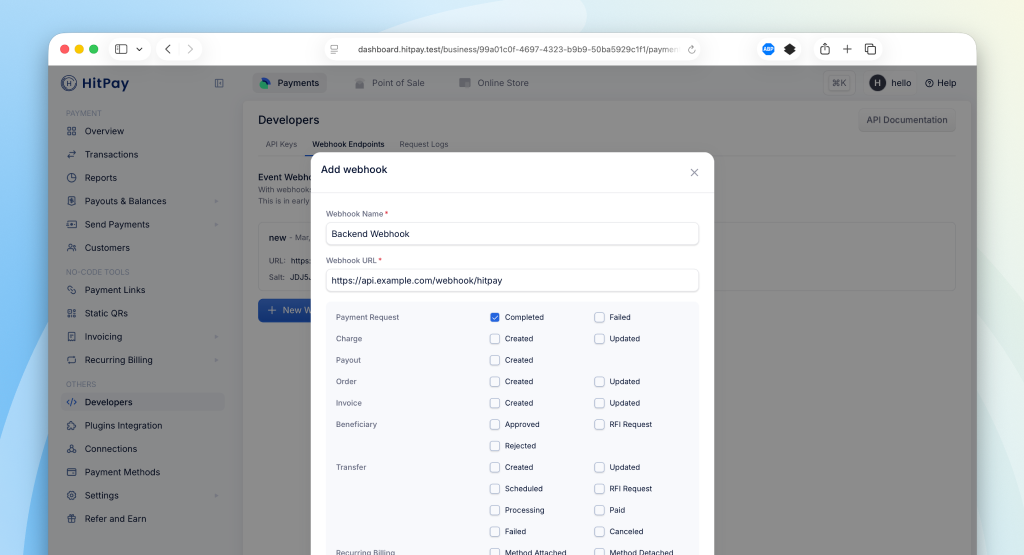
After the payment is processed, HitPay sends a webhook to your server with the payment status.Register Your Webhook
To receive payment notifications, register a webhook URL from your HitPay Dashboard:- Navigate to Developers > Webhook Endpoints in your dashboard
- Click on New Webhook
- Enter a name and your webhook URL
- Select the
payment_request.completedevent - Save your webhook configuration
Webhook Payload
When a payment is completed, HitPay sends a JSON payload to your registered webhook URL with the following headers:| HTTP Header | Description |
|---|---|
| Hitpay-Signature | HMAC-SHA256 signature of the JSON payload, using your salt value |
| Hitpay-Event-Type | completed |
| Hitpay-Event-Object | payment_request |
| User-Agent | HitPay v2.0 |
Sample Webhook Payload
Validating the Webhook
To ensure the webhook is authentic, validate theHitpay-Signature header:
Next Steps
Now that you understand the basics of in-person payments:- Learn how to handle failed payment requests
- Get started with testing in Sandbox
FAQs
What about the 'webhook' parameter in the API?
What about the 'webhook' parameter in the API?
The
webhook parameter in the payment request API is deprecated and will be removed in a future version.Why the change?- The new registered webhook system supports JSON payloads with richer data
- You can subscribe to multiple event types (not just payment completion)
- Centralized management from your dashboard
- Better scalability - one webhook URL handles all your payment requests
- Register your webhook URL in Developers > Webhook Endpoints
- Subscribe to
payment_request.completedevent - Update your webhook handler to accept JSON payloads
- Remove the
webhookparameter from your API calls
Does the in-person payments API support the Wisepad3 reader?
Does the in-person payments API support the Wisepad3 reader?
No, these APIs only work with Wi-Fi readers.
Can I connect a Bluetooth printer to my Wi-Fi terminal?
Can I connect a Bluetooth printer to my Wi-Fi terminal?
No, you cannot connect a Bluetooth printer to the Wi-Fi terminal.
How does the card reader know whether to show QR code or accept card payment?
How does the card reader know whether to show QR code or accept card payment?
The card reader automatically detects the payment method. When you create a payment request, the reader will display a QR code first. If the customer prefers to pay with a card, they can simply insert or tap their card on the reader.
Which QR payment methods are supported?
Which QR payment methods are supported?
The supported QR payment methods depend on your business location and the payment networks available in your region. Common methods include PayNow (Singapore), Ingenicos (PHP), PromptPay (Thailand), and other local QR payment schemes. See the complete list of supported QR payment methods.
Can I test the APIs in a sandbox using a test card or simulator?
Can I test the APIs in a sandbox using a test card or simulator?
Yes, you can test in Sandbox! However, the APIs do not support a virtual simulator. To test successfully:
- For Card Payments: You’ll need a physical test card. Contact HitPay support to obtain test cards for your region.
- For QR Payments: You can test with QR code payments using your mobile payment app, as these don’t require physical cards.
Why does my charges `webhook status` show as failed?
Why does my charges `webhook status` show as failed?
If you are using a payment plugin, after every successful payment, a webhook is sent to your store to acknowledge the payment confirmation. Your order is marked as paid through this webhook.A webhook status showing as "failed" indicates that Hitpay failed to communicate with your server. This can happen for the following reasons:
- Your store may have a security feature that blocked Hitpay's request.
- Your server was unavailable during this time.
- Production:
3.1.13.32,52.77.254.34 - Sandbox:
54.179.156.147